Day 27: Mastering Terraform Architecture
Mar 30, 2025
•02:03 AM GMT+8

In this blog, we will explore the architecture of Terraform, understanding how it functions and why it is widely used in Infrastructure as Code (IaC). We will discuss Terraform's declarative approach, compare it with imperative methods, examine how it differs from ARM templates, and break down its ecosystem. By the end of this blog, you’ll have a solid foundation of Terraform’s structure before diving into practical applications in the next blogs.
What is Terraform?

Terraform is an open-source IaC tool created by HashiCorp. It allows developers and system administrators to define, manage, and provision infrastructure using a simple, human-readable configuration language called HCL (HashiCorp Configuration Language).
Terraform can be used to manage resources across multiple cloud providers such as Azure, AWS, GCP, and even on-premises infrastructure.
Key Features of Terraform:
- Declarative Configuration – Define the desired state of infrastructure, and Terraform ensures it is provisioned accordingly.
- Multi-cloud Support – Works with Azure, AWS, GCP, and various other platforms.
- State Management – Maintains the current state of infrastructure to track changes.
- Modular and Reusable Code – Allows reusability with modules for efficient management.
Terraform is Declarative
When it comes to defining infrastructure, Terraform follows a declarative approach. In other words, you specify what kind of end state you want your infrastructure to be in and Terraform takes care of achieving that end state. It is not necessary to describe how to reach that state, just what the final infrastructure should look like.
For example, if you want to create a virtual machine (VM) in Azure, you define its configuration in a Terraform file, and Terraform ensures it is created with the specified settings.
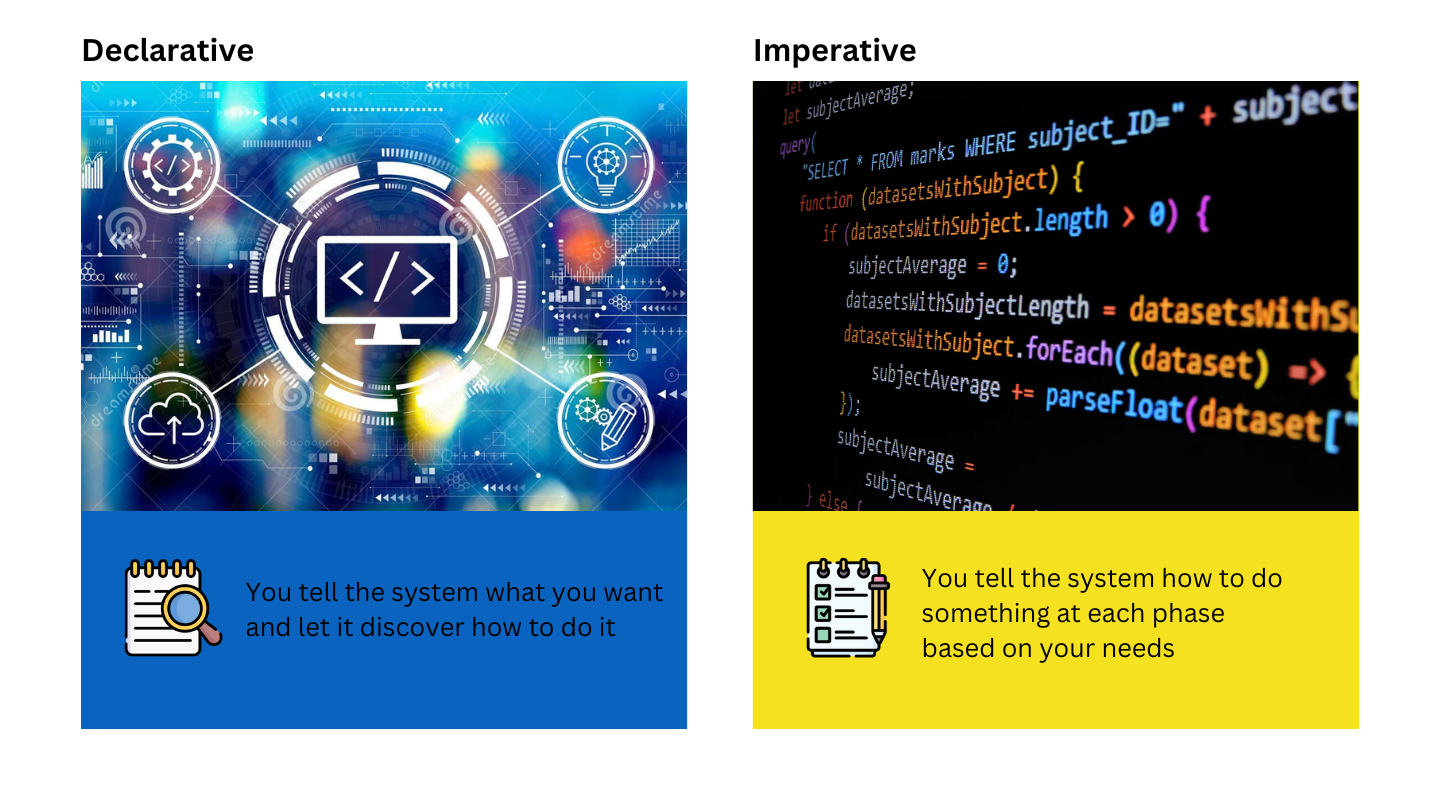
Declarative vs Imperative
Left Photo by Melpomenem / Dreamstime, Right Photo by Gabriel Heinzer / Unsplash
Terraform’s declarative nature contrasts with the imperative approach used in scripting languages like Bash or PowerShell.
Example:
Declarative Approach - Terraform
resource "azurerm_storage_account" "example" {
name = "examplestorage"
resource_group_name = "example-rg"
location = "eastus"
account_tier = "Standard"
account_replication_type = "LRS"
}This defines what you want (a storage account with specific properties), and Terraform determines how to apply it.
Imperative Approach - Powershell
New-AzStorageAccount -ResourceGroupName "example-rg" -Name "examplestorage" -Location "eastus" -SkuName "Standard_LRS"This executes a step-by-step command that must be run manually to create the storage account.
ARM Templates vs Terraform
ARM (Azure Resource Manager) Templates are another way to define infrastructure on Azure, but they differ from Terraform in key ways.
| Feature | ARM Templates | Terraform |
| Language | JSON-based | HCL (HashiCorp Configuration Language) |
| Declarative | Yes | Yes |
| State Management | No state management | Uses a state file |
| Reusability | Less modular | Highly modular with modules |
| Multi-cloud Support | Azure-only | Works with Azure, AWS, GCP, etc. |
Terraform Ecosystem
Terraform is an open-source tool with a well-structured ecosystem that includes its codebase, public registry, and documentation.
| Component | Description |
| Terraform Codebase | Terraform’s full source code is open-source and available on GitHub: github.com/hashicorp/terraform. You can explore the latest updates, bug fixes, and submitted issues. |
| Public Registry | A collection of providers and modules for multiple cloud providers (Azure, AWS, GCP) and other technologies. You can search and discover reusable infrastructure components. |
| Documentation | Available on the official Terraform website. Includes tutorials, certification training, and best practices for managing infrastructure. |
Terraform Terms
| Term | Description |
| Terraform File | .tf files that define infrastructure using HCL (HashiCorp Configuration Language). |
| Terraform Project | A directory containing .tf files and configurations for managing infrastructure. |
| Resources | Individual components like VMs, storage, and networking managed by Terraform. |
| Providers | Cloud platforms (Azure, AWS, GCP) that Terraform interacts with to provision resources. |
| Variables | Configurable values used in Terraform files to allow flexibility and reuse. |
| Input Variables | Special variables that allow users to pass values dynamically into Terraform configurations. |
| Modules | A way to group multiple Terraform resources into reusable infrastructure components. |
Terraform Workflow Overview
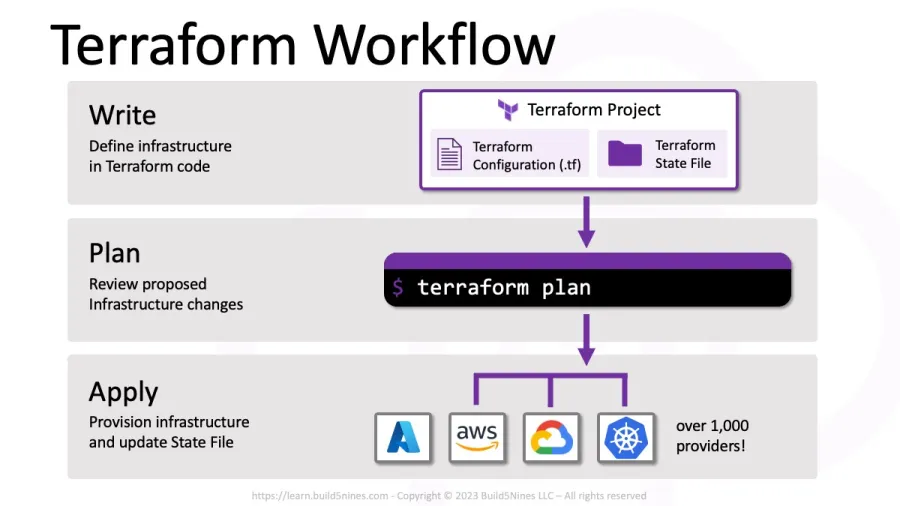
Photo by Chris Pietschmann / Build5Nines
Terraform follows a straightforward workflow consisting of three main stages: Write, Plan, and Apply.
- Write – Define the desired state of infrastructure using HashiCorp Configuration Language (HCL) in
.tffiles. This includes specifying resources, providers, and configurations. - Plan – Terraform analyzes the configuration and generates an execution plan. This step helps preview changes before applying them, ensuring that the desired modifications are correct.
- Apply – Terraform executes the plan, provisioning or modifying infrastructure to match the defined state. Changes are applied securely and efficiently.
Task: Getting Started with Terraform
Step 1: Install Terraform
Download and install Terraform from the official Terraform website
Step 2: Install VS Code Terraform Extension
- Open VS Code.
- Go to Extensions (
Ctrl + Shift + X). - Search for "Terraform" and install the extension.
Step 3: Explore the Azure Provider
Terraform offers a wide range of providers that allow ideal interaction with various cloud platforms and services. Providers act as a bridge between Terraform and the underlying infrastructure, enabling users to manage resources efficiently using IaC.
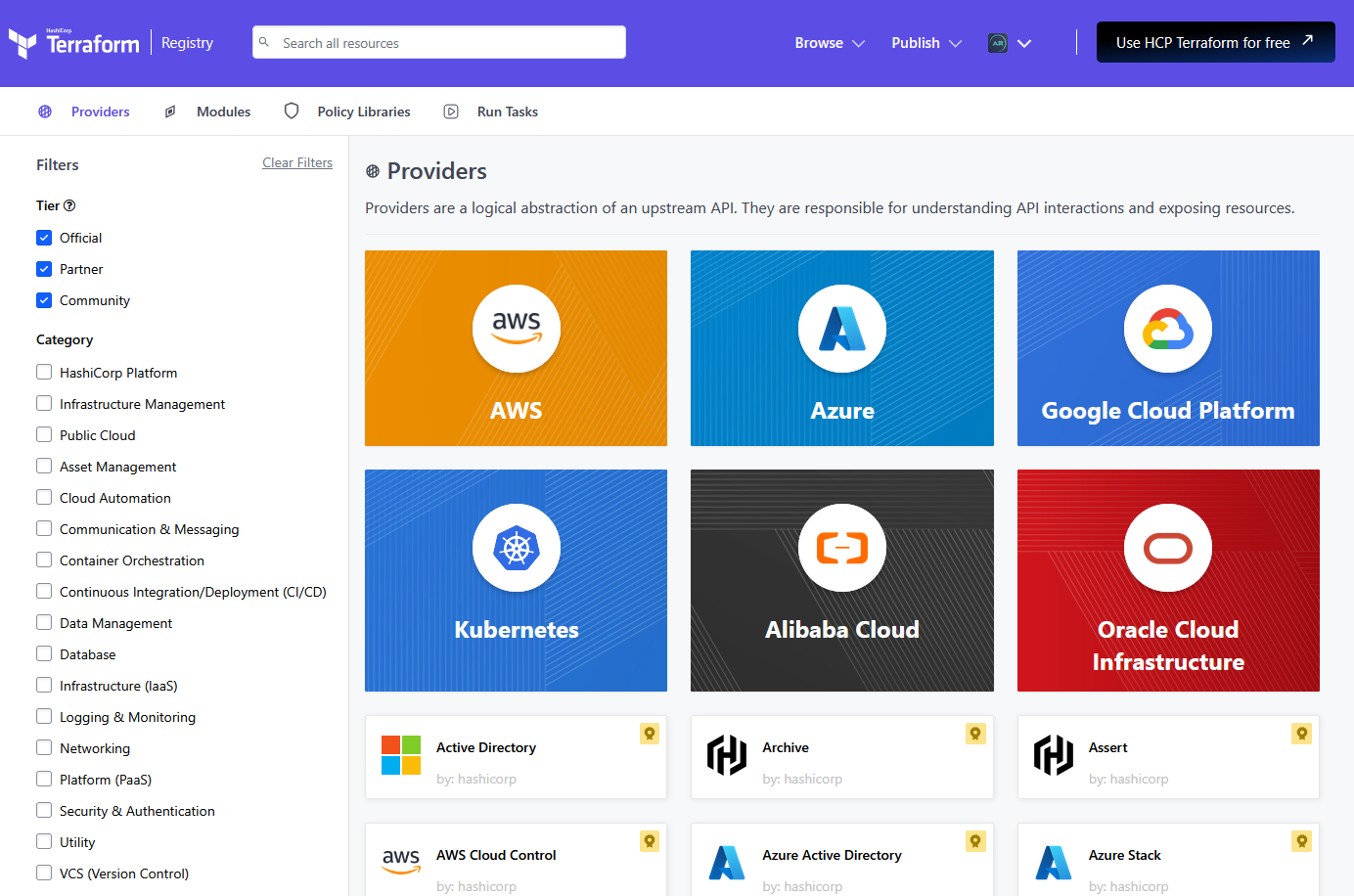
As shown in the image, Terraform supports multiple providers such as Azure, AWS, Google Cloud Platform (GCP), Kubernetes, and many more!
These providers simplify cloud resource management by offering pre-built modules and APIs, making it easier to deploy and maintain infrastructure using Terraform. By leveraging these providers, users can define, provision, and manage resources across multiple cloud platforms in a consistent and automated way.
Using the Azure Provider in Terraform
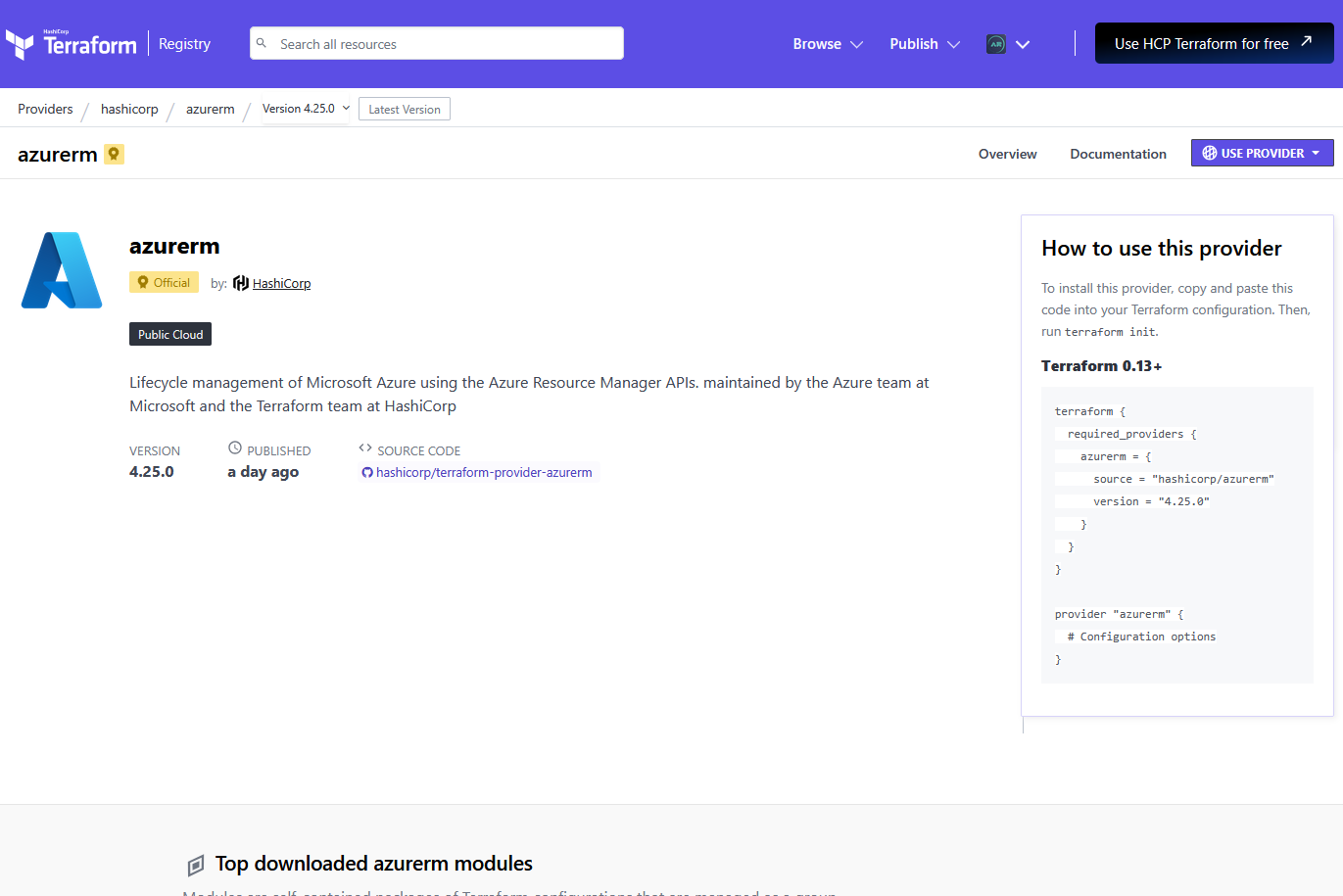
For the rest of the future blog, we will use Azure as our cloud provider. Terraform provides an official Azure Resource Manager (azurerm) provider that allows users to manage Azure infrastructure using Terraform.
Below is an example of how to define the Azure provider in Terraform:
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "4.25.0"
}
}
}
provider "azurerm" {
# Configuration options
}This configuration ensures that Terraform pulls the correct Azure provider version and enables Terraform to interact with Azure resources.
Step 4: Terraform Initialization
In this task, we will initialize Terraform using VS Code. The initialization process is the first step in setting up Terraform to manage infrastructure, ensuring that all required providers and modules are properly downloaded.
Setting Up Terraform in VS Code
- Create a New Folder named
01-HelloWorld. - Create the
main.tffile inside01-HelloWorld. - Add the Azure Provider Configuration. Copy and paste the sample code above.
- Run the Terraform initialization command inside
01-HelloWorlddirectory:
terraform initAfter executing this command, Terraform will download the Azure provider and create necessary configuration files.
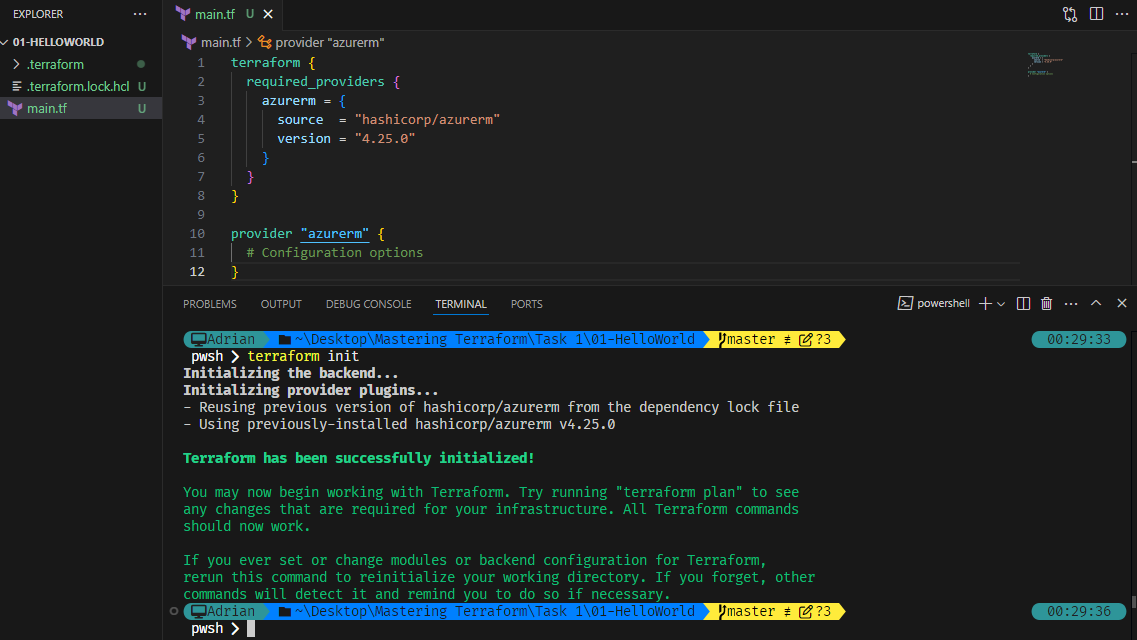
What Happens After Running terraform init?
After initialization, Terraform automatically creates the following files and folders inside 01-HelloWorld:
| File/Folder | Description |
.terraform/ | A directory where Terraform stores provider plugins and metadata. |
.terraform.lock.hcl | A lock file that ensures consistent provider versions across environments. |
Explanation of Generated Files
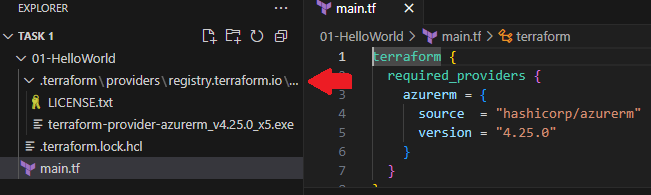
.terraform/ Folder
- This folder contains all the downloaded provider files and dependency information.
- It ensures that Terraform can work offline without needing to download the provider again unless updated.
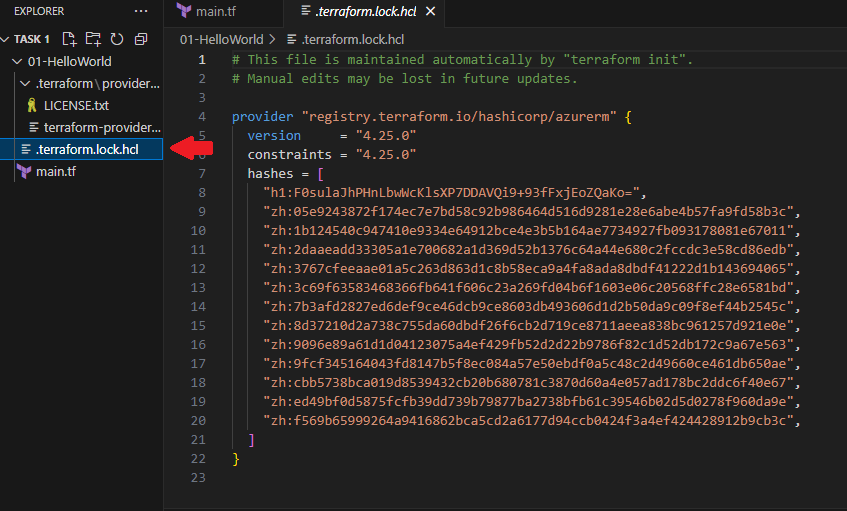
.terraform.lock.hcl File
- This lock file keeps track of specific provider versions to prevent unexpected updates.
- It ensures that Terraform uses the same provider versions across different environments, avoiding compatibility issues.
Why is This Important?
At this stage, we have only set up Terraform for Azure. The main.tf file currently contains only the provider configuration.
By running terraform init, Terraform:
- Downloaded the Azure provider and stored it in
.terraform/ - Created a lock file to maintain version consistency
Conclusion
In this blog, we explored Terraform’s architecture, its declarative approach, and how it compares to imperative methods and ARM templates. We also discussed the Terraform ecosystem, key concepts like providers, resources, and modules, and the Terraform workflow (Write > Plan > Apply).
Additionally, we demonstrated how to set up Terraform in VS Code, initialize the Azure provider, and understand the .terraform directory and lock file.
In the next blog, we will explore Terraform basics, including key commands and how to create and apply Terraform configurations.
Day 27: Mastering Terraform Architecture
Learn Terraform architecture, declarative vs imperative, Terraform ecosystem, Azure provider setup, and first initialization.
For the passion of automated cloud solutions.
Subscribe to get the latest posts. I mostly write about Backend (Python/Bash), DevOps and Linux.