Day 30: Mastering Terraform State
Apr 17, 2025
•07:10 PM GMT+8

Terraform uses a state file (terraform.tfstate) to keep track of infrastructure resources that it manages. This state acts as a source of truth for your Terraform project, allowing it to know what is currently deployed and how to compare it with future changes.
Understanding and managing state properly is crucial in avoiding misconfigurations, especially in collaborative environments or production systems.
Purpose of State
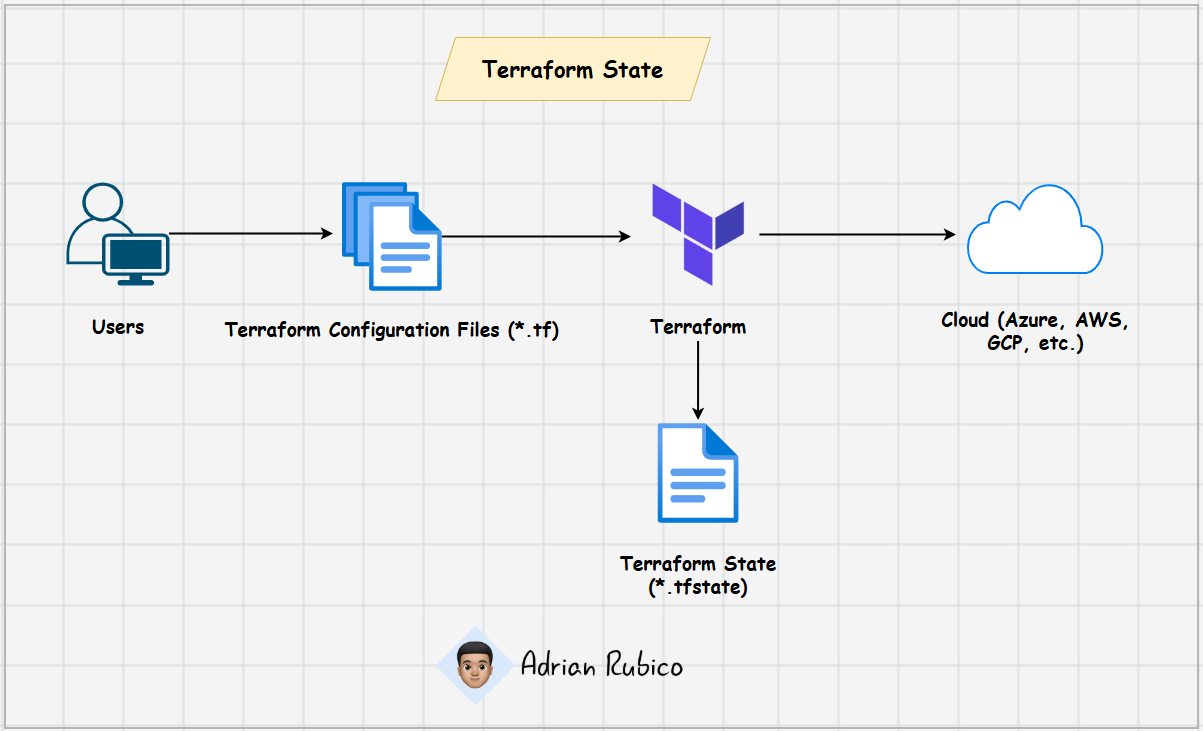
Terraform state is essential because it is a critical component that tracks the current state of the infrastructure as defined in the Terraform configuration. It serves several key purposes:
- Maps configuration to real-world infrastructure.
- Tracks metadata and resource dependencies.
- Determines the necessary actions during
plan,apply, ordestroy.
Without state, Terraform would have to query the entire infrastructure, which is inefficient and error-prone.
Task
As a prerequisite, clone the Terraform template from my GitHub repository under the folder 02-State. This will provide the base configuration for our work.
https://github.com/git-adrianrubico/learn-terraform/tree/master
cd learn-terraform/02-State💡 Note: After cloning the repository, make sure to copy the
terraform.tfstatefile from the previous blog folder01-HelloWorld. If not available, please initialize and generate a new one by runningterraform init>terraform plan>terraform apply.
Now, let's explore a few Terraform state commands.
terraform state list
This command to list all resources currently tracked in the state file:
terraform state list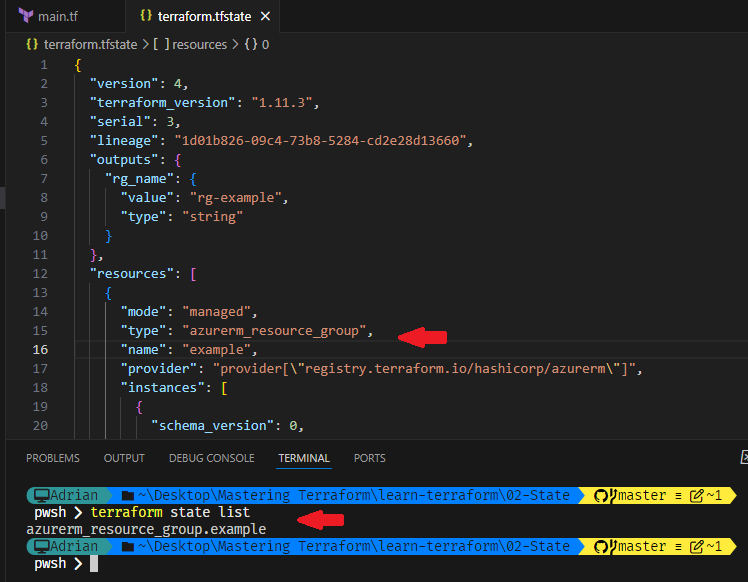
terraform state mv
We will rename the existing resource from azurerm_resource_group.example to azurerm_resource_group.rg-example using the move command:
terraform state mv azurerm_resource_group.example azurerm_resource_group.rg-example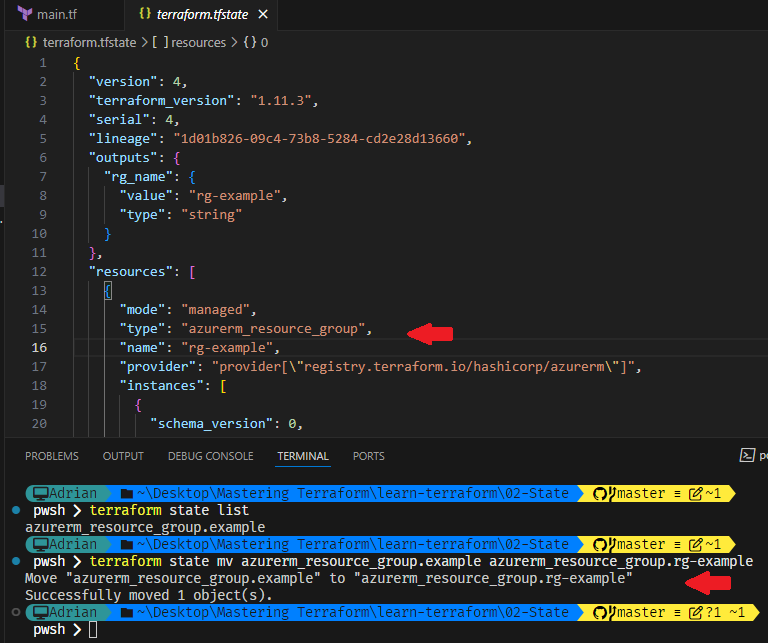
Useful for renaming or restructuring resource labels without destroying and recreating them.
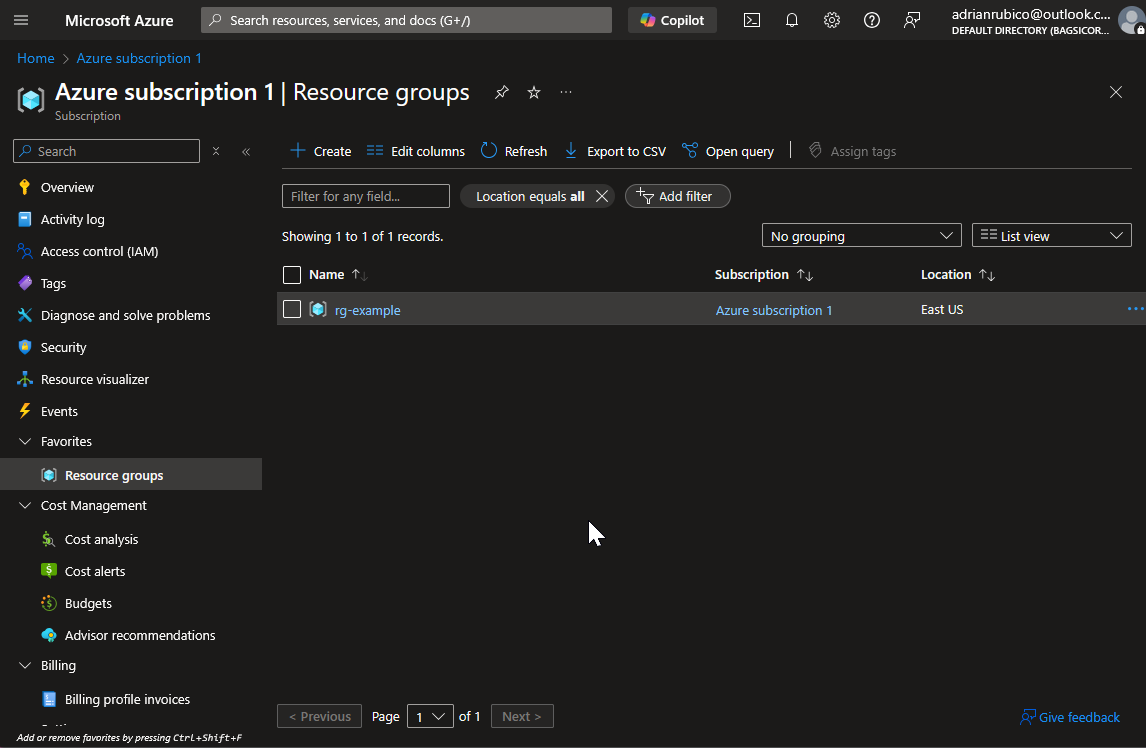
Create an Azure Storage Account
Now update your main.tf to include a storage account resource:
resource "azurerm_resource_group" "rg-example" {
name = "rg-example"
location = var.azregion
tags = {
environment = local.env
}
}
resource "azurerm_storage_account" "sa-example" {
name = "stgacsample${local.env}01"
resource_group_name = azurerm_resource_group.rg-example.name
location = azurerm_resource_group.rg-example.location
account_tier = "Standard"
account_replication_type = "GRS"
tags = {
environment = local.env
}
}📌Note: The storage account name must be globally unique. If you receive a name conflict error, simply change the name to something more unique (e.g., add a random suffix or use your initials).
Also, update outputs.tf to show information about the new storage account:
output "rg_name" {
value = azurerm_resource_group.rg-example.name
}
output "sa_name" {
value = azurerm_storage_account.sa-example.name
}Apply the Configuration
Run the following command to apply changes:
terraform apply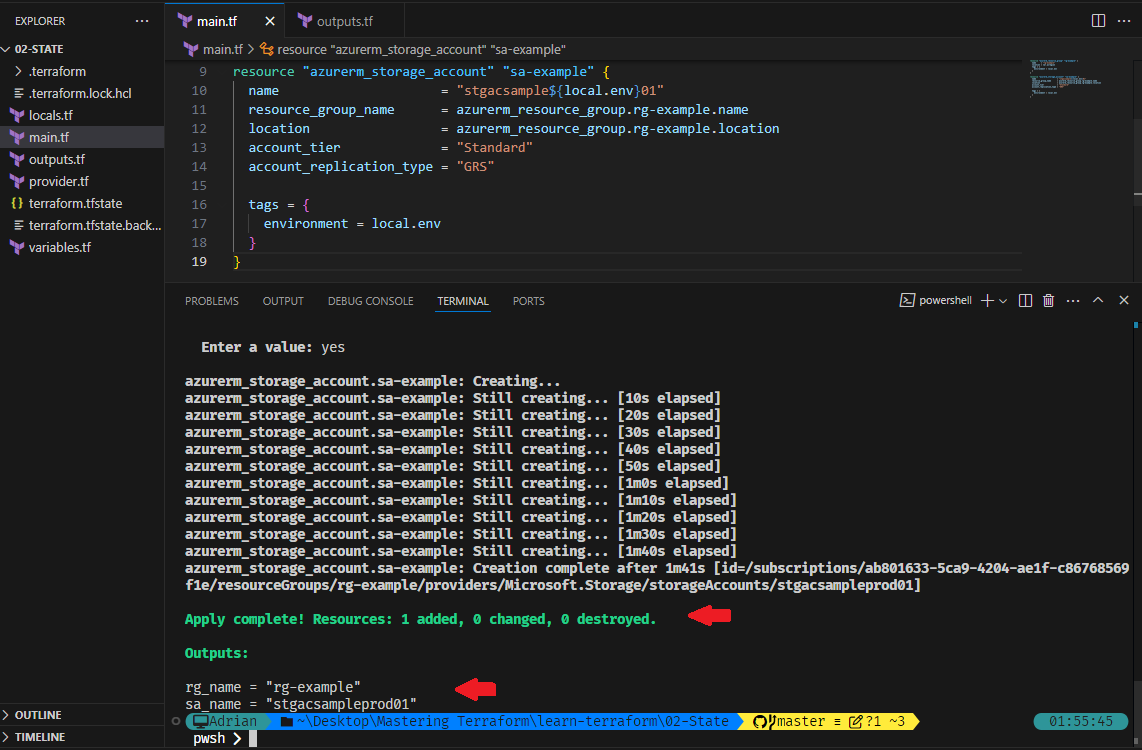
Verify the created resource in Azure Portal:
terraform state show
Displays detailed attributes of a specific resource in state. This will show values like id, name, location, tags, and etc.
terraform state show azurerm_storage_account.sa-example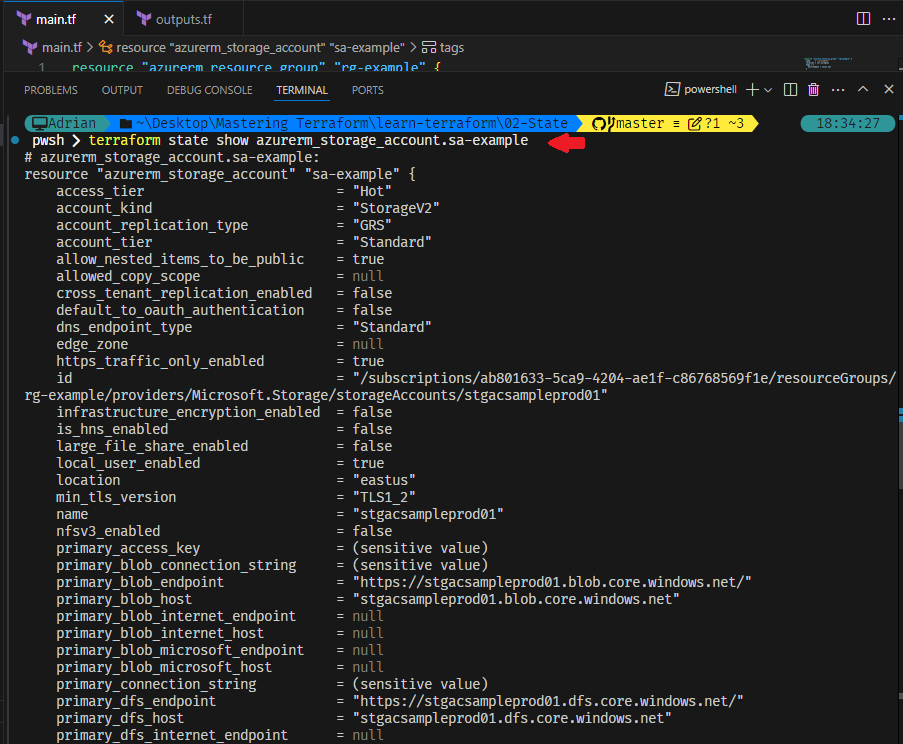
terraform state rm
Removes a resource from the state file (without destroying the actual resource).
terraform state rm azurerm_storage_account.sa-example⚠️ Be careful! Terraform will forget this resource and try to recreate it on the next apply.
Terraform State Considerations
Terraform stores its state in a file called terraform.tfstate . This file is crucial because it maps real-world infrastructure to your configuration. Managing this state file securely and effectively is critical, especially in team environments or production systems.
- Azure: Use an Azure Storage Account with a container for the state file and enable blob locking.
- AWS: Store the state in an S3 bucket with encryption and versioning. Use DynamoDB for state locking.
⚠️ The state file can contain sensitive information such as secrets, credentials, or IP addresses. Make sure it's stored securely with restricted access.
💡 We will explore this more deeply in the upcoming blog, where we’ll learn about Terraform backends and how to apply the state file remotely using Azure Storage.
Conclusion
We explored the inner workings of Terraform state. We learned how to list and show state data, rename state entries, and securely manage the state file. We also created an Azure Storage Account as part of the exercise.
In the next blog, we will dive into Terraform Provisioners ,which allow you to execute scripts or commands during resource creation or destruction.
Day 30: Mastering Terraform State
Learn how Terraform manages state, its purpose, essential commands, and best practices for secure remote storage.
For the passion of automated cloud solutions.
Subscribe to get the latest posts. I mostly write about Backend (Python/Bash), DevOps and Linux.